Introduction
The Open Systems Interconnection model (OSI model), created by the International Organization for Standardization, serves as a conceptual framework that defines and standardizes the communication functions within a telecommunication or computing system, irrespective of its internal structure and technology. Its primary objective is to achieve interoperability among diverse communication systems through the use of standard protocols.
This model organizes a communication system into distinct abstraction layers, with the initial version specifying seven layers.
What is the significance of the OSI model?
Even though the contemporary Internet doesn't strictly adhere to the OSI Model, leaning more towards the simpler Internet protocol suite, the OSI Model remains highly valuable for diagnosing network issues. Whether it's an individual struggling to connect their laptop to the Internet or a widespread outage affecting thousands of users, the OSI Model proves instrumental in dissecting the problem and pinpointing its origin. By narrowing down the issue to a specific layer of the model, it becomes possible to streamline troubleshooting efforts and avoid unnecessary work.
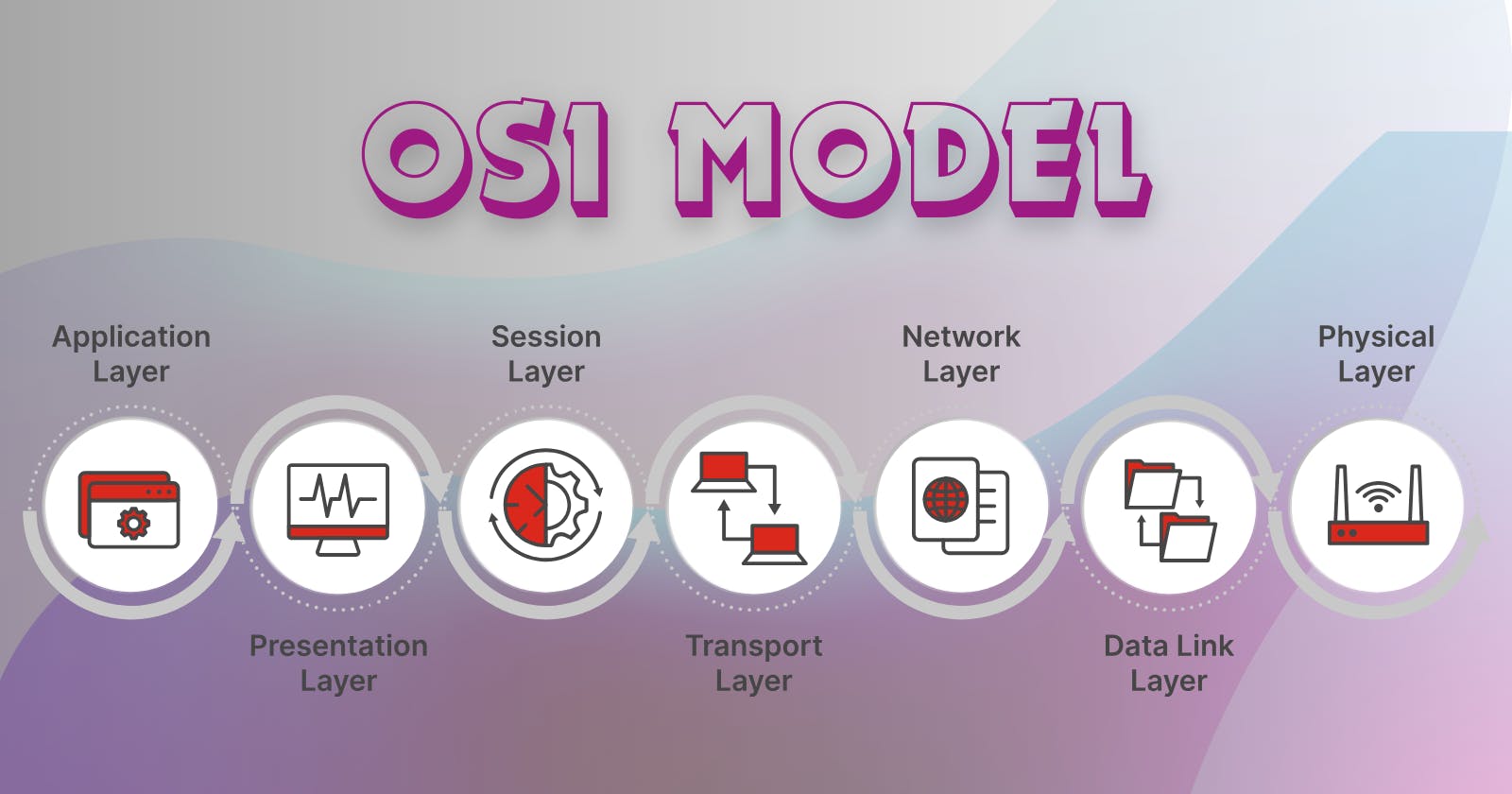
The 7 layers of the OSI Model
The seven layers of the OSI model can be delineated in the following order, from top t bottom:-
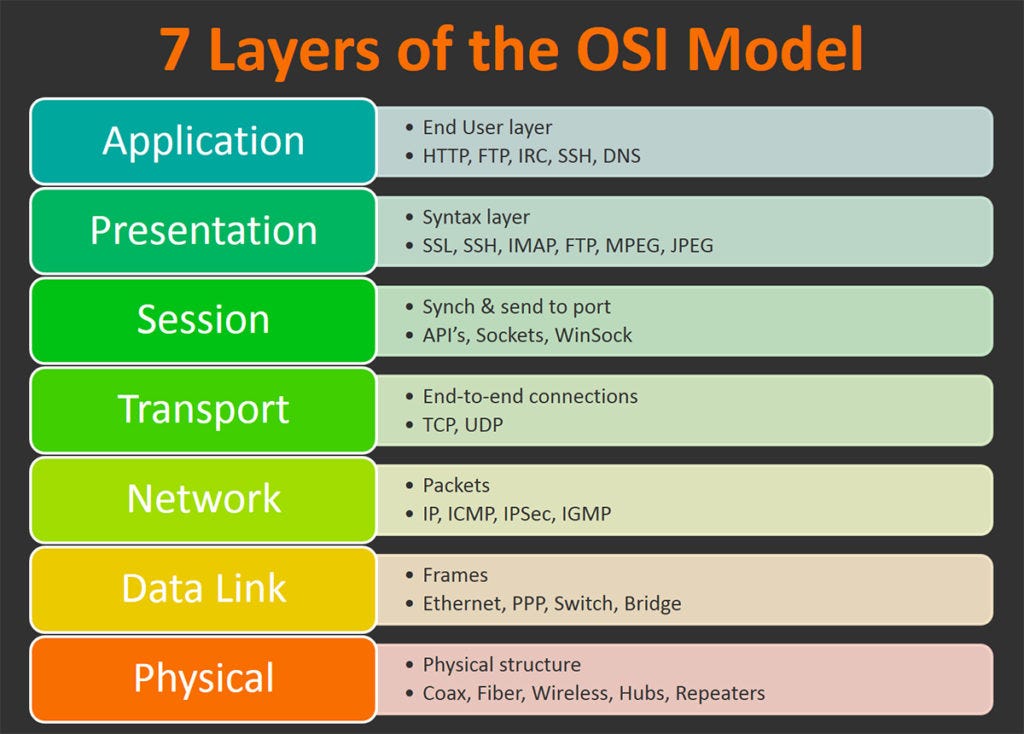
Layer 7 - The Application Layer
The application layer stands as the sole layer that directly engages with user data. Software applications such as web browsers and email clients depend on the application layer to initiate communication. It's important to note that client software applications themselves are not part of the application layer. Instead, the application layer is responsible for managing the protocols and data manipulation essential for the software to present meaningful information to the user.
A few examples of application layer protocols are the Hypertext Transfer Protocol (HTTP), File Transfer Protocol (FTP), Post Office Protocol (POP), Simple Mail Transfer Protocol (SMTP), and Domain Name System (DNS).
Layer 6 - The Presentation Layer
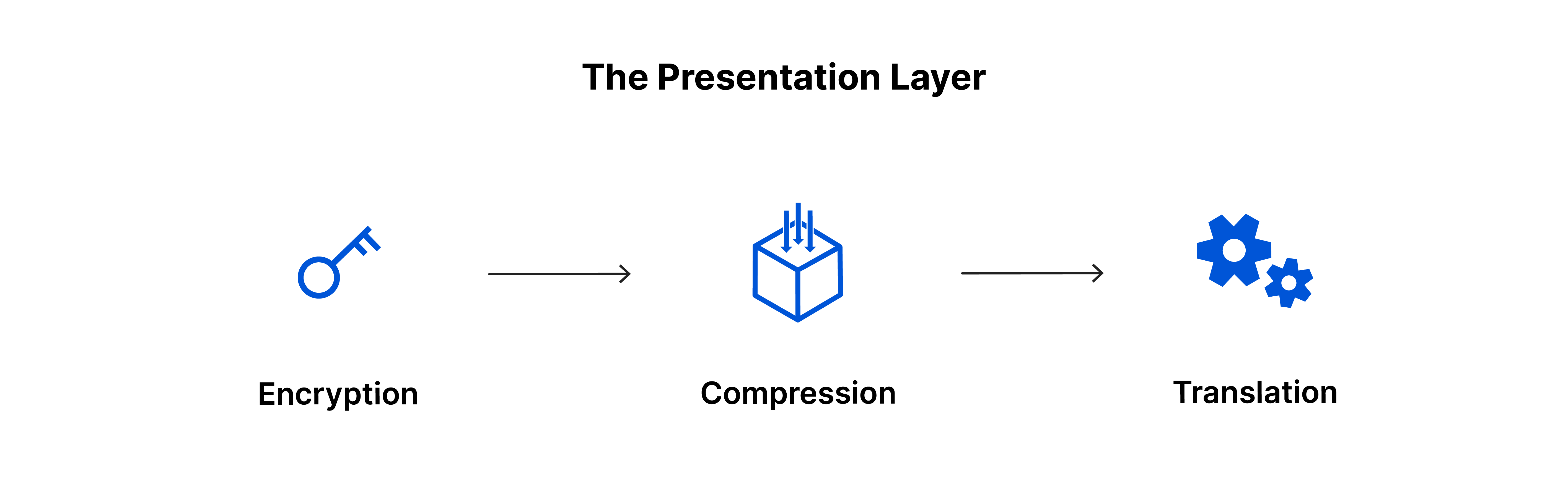
The presentation layer prepares data for the application layer. It defines how two devices should encode, encrypt, and compress data so it is received correctly on the other end. The presentation layer takes any data transmitted by the application layer and prepares it for transmission over the session layer.
Layer 6 acts as a crucial intermediary, translating data into a compatible syntax for the application layer of the receiving device. In encrypted connections, it handles both encryption on the sender's end and decryption on the receiver's end, ensuring the application layer receives readable data. Additionally, the presentation layer compresses data from the application layer before passing it to layer 5, optimizing communication efficiency.
A few examples of Presentation layer protocols are XDR (External Data Representation), TLS(Transport Layer Security), SSL(Secure Socket Tunneling) etc.
Layer 5 - The Session Layer
The session layer creates communication channels, called sessions, between devices. It is responsible for opening sessions, ensuring they remain open and functional while data is being transferred, and closing them when communication ends.
The session layer can also set checkpoints during a data transfer—if the session is interrupted, devices can resume data transfer from the last checkpoint. For example, if a 50 megabyte file is being transferred, the session layer could set a checkpoint every 5 megabytes. In the case of a disconnect or a crash, after 22 megabytes have been transferred, the session could be resumed from the last checkpoint, meaning only 30 more megabytes of data need to be transferred. Without the checkpoints, the entire transfer would have to begin again from scratch.
A few examples of Session layer protocols are SMB(Server Message Block), NCP(NetWare Core Protocol), iSNS(Internet Storage Name Service), etc..
Layer 4 - The Transport Layer
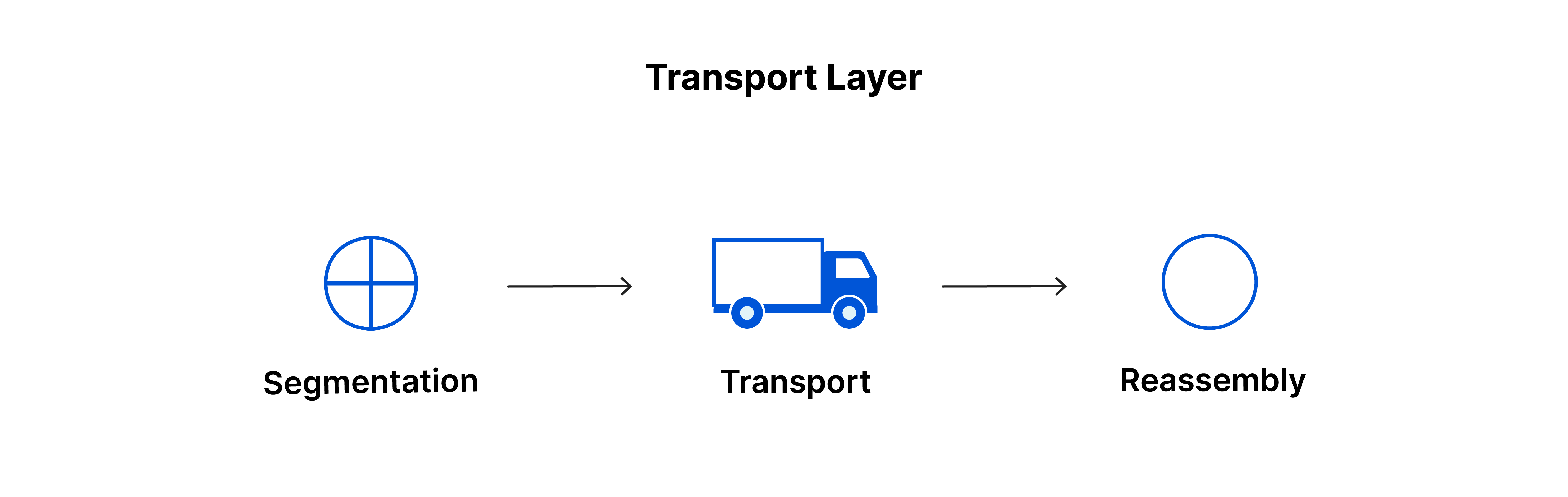
The transport layer plays a crucial role in the data transfer process initiated in the session layer. It divides the data into "segments" during transmission and is responsible for reassembling these segments on the receiving end, converting them back into usable data for the session layer.
Additionally, the transport layer manages flow control, ensuring data is sent at a rate compatible with the receiving device's connection speed such that a fast connection does not overwhelm a receiver with a slow connection. It also oversees error control, verifying the accuracy of received data and requesting retransmission if needed.
Transport layer protocols include the Transmission Control Protocol (TCP) and the User Datagram Protocol (UDP), DCCP(Datagram Congestion Control Protocol), etc...
Layer 3 - The Network Layer
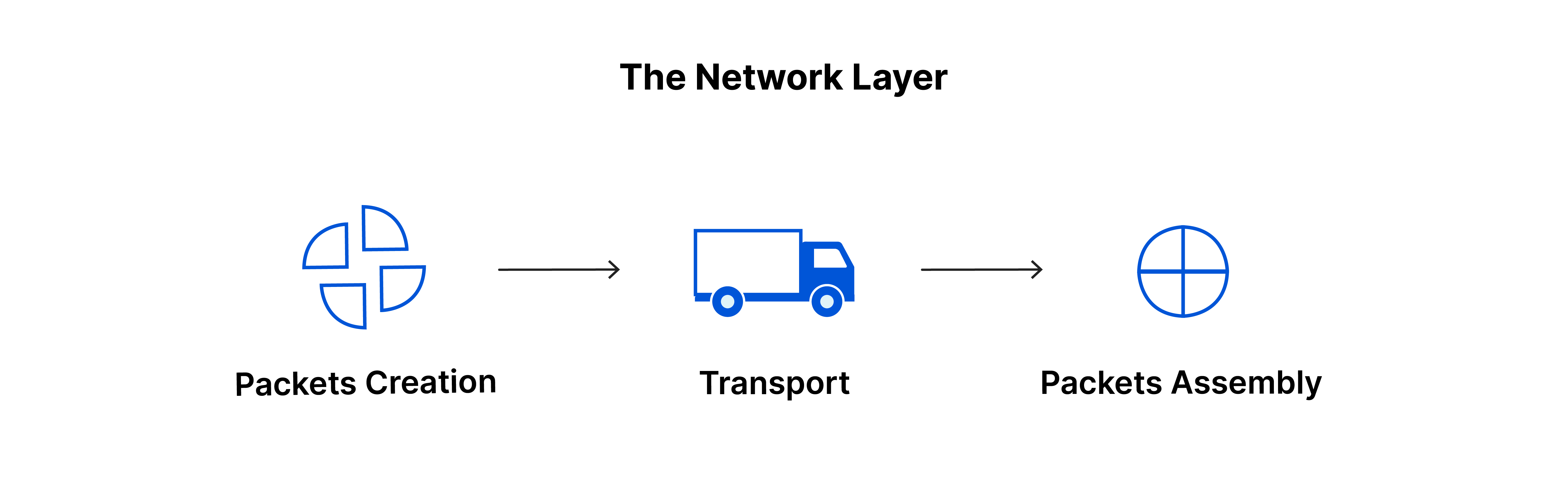
The network layer plays a vital role in enabling data transfer between distinct networks. If two communicating devices reside on the same network, the network layer becomes needless.
It fragments segments from the transport layer into smaller units, referred to as packets, on the sender's device and reassembles these packets on the receiving device. Additionally, the network layer determines the optimal physical path for data to reach its destination, a process known as routing.
Protocols associated with the network layer include IP, ICMP (Internet Control Message Protocol), IGMP (Internet Group Message Protocol), etc...
Layer 2 - The Data Link Layer
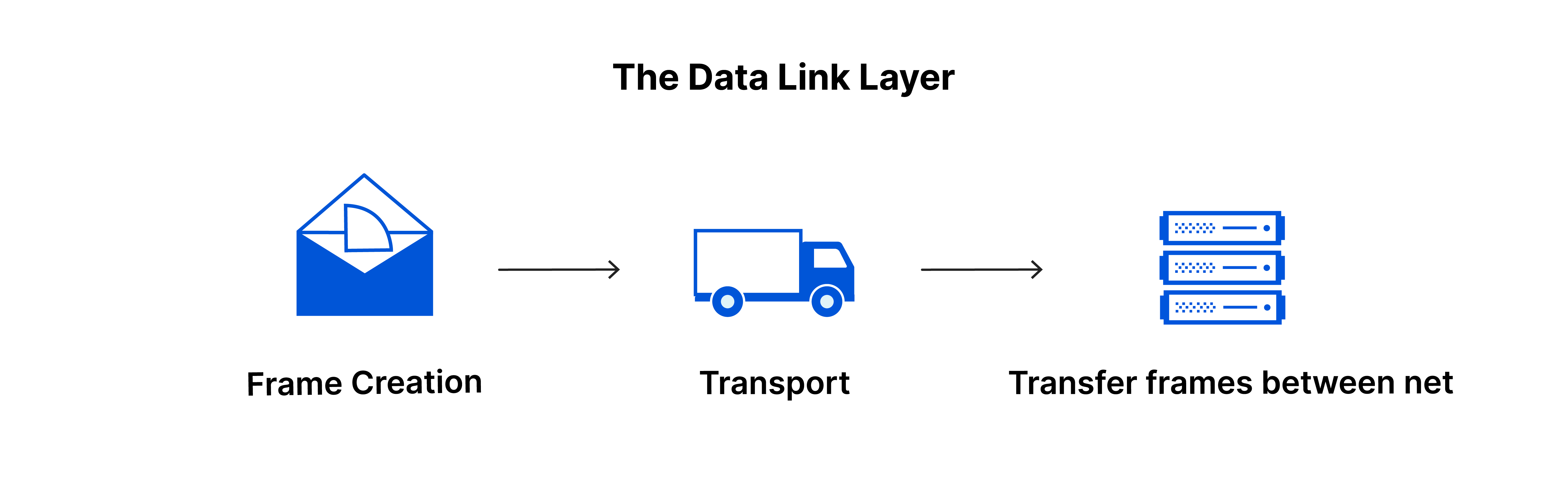
The data link layer closely resembles the network layer but is specifically designed for managing data transfer between two devices within the same network. This layer receives packets from the network layer and subdivides them into smaller units known as frames. Similar to the network layer, the data link layer oversees flow control and error control in intra-network communication, distinguishing itself from the transport layer, which focuses on these aspects in inter-network communications only.
This layer is composed of two parts—
Logical Link Control (LLC), which identifies network protocols, performs error checking and synchronizes frames, and
Media Access Control (MAC) which uses MAC addresses to connect devices and define permissions to transmit and receive data.
Layer 1 - The Physical Layer
The physical layer manages the actual physical connection, whether it's through cables or wireless links, between network nodes. It specifies the connectors and the electrical or wireless technology linking devices. This layer oversees the transmission of raw data, consisting of 0s and 1s, and ensures effective bit rate control.
Advantages of the OSI Model
The OSI model offers valuable advantages for both users and operators of computer networks:
Network Planning:
Facilitates users and operators in determining the necessary hardware and software components to construct their network effectively.
Process Understanding:
Enhances comprehension and communication regarding the processes involved in components communicating across a network.
Troubleshooting Capabilities:
Enables efficient troubleshooting by pinpointing the specific network layer causing an issue, allowing focused efforts on resolution.
For network device manufacturers and software vendors:
Interoperability:
Facilitates the creation of devices and software that can seamlessly communicate with products from any vendor, promoting open interoperability.
Product Scope Definition:
Aids in defining which parts of the network a product should work with, ensuring compatibility and functionality.
Clarity in Communication:
Assists in clearly communicating to users the specific network layers at which their product operates, whether solely at the application layer or across the entire stack.
Conclusion
In summary, the OSI model provides a structured blueprint for seamless data communication. Navigating through its layers, from user interfaces to raw data transmission, it elucidates the organized pathways crucial for efficient digital interactions. As a guide for troubleshooting, ensuring interoperability, and comprehending data transfer nuances, the OSI model continues to play a pivotal role in the dynamic realm of technology.
Endcard
Thank you for joining me on this insightful blog on the OSI Model
If you found this blog helpful and informative, don't forget to give it a like!
Stay updated with my latest posts and never miss out on exciting content! Click that Follow button to join and stay in the loop!
Follow me on Linkedin --> rupak1chakraborty
Stay tuned for more such content...👋🔍🌈