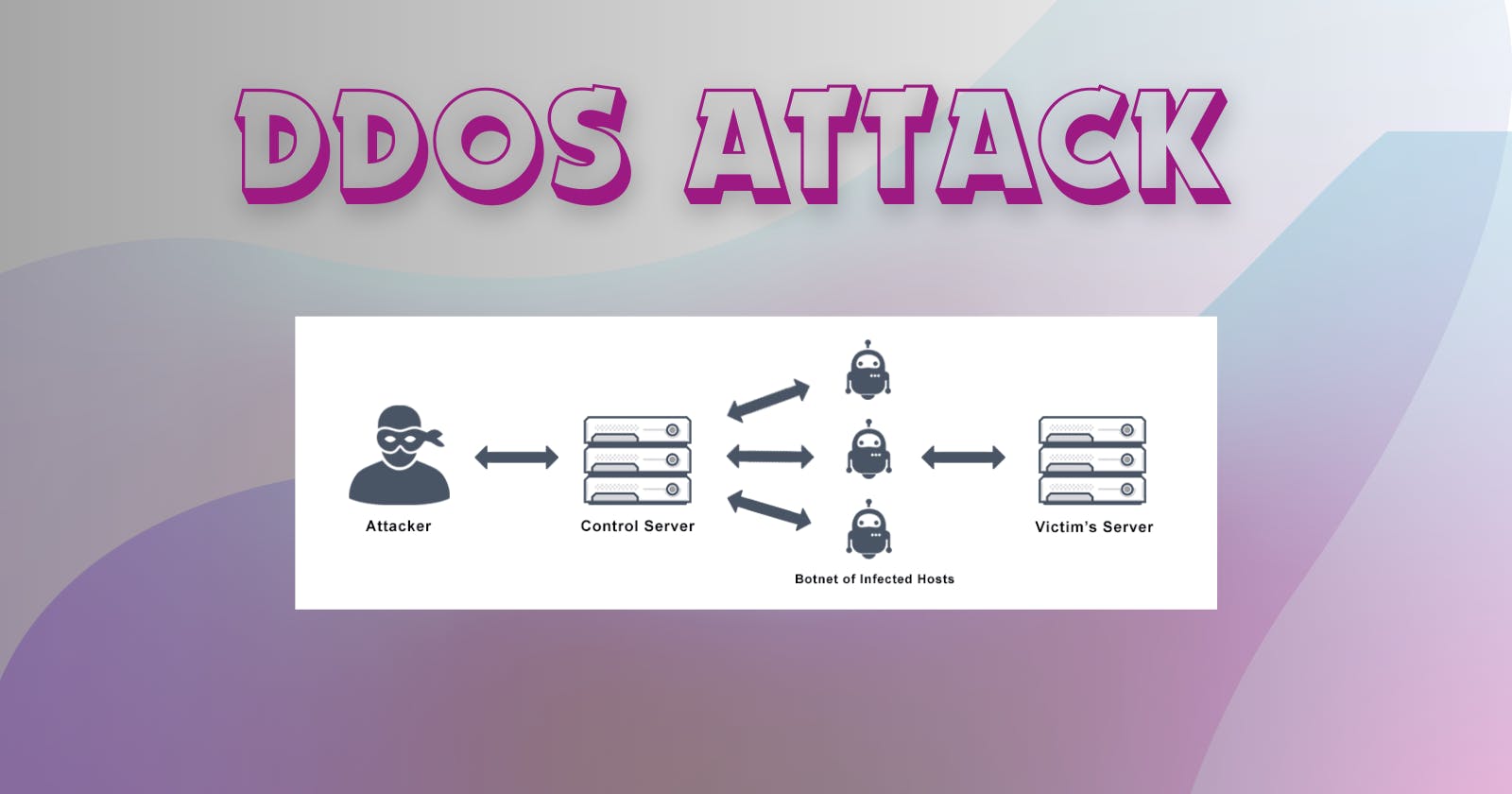
DDoS Attack
Understanding DDoS Attacks and Fortifying the Digital Fortress
Table of contents
Introduction
In the rapidly evolving cyber landscape of today, risks and vulnerabilities are undergoing continuous transformations. This digital realm, while remaining expansive and interconnected, houses shadows that demand our attention.
Among these, the Distributed Denial of Service (DDoS) attack stands out as a notable and frequently discussed phenomenon.
In this blog, we delve into the intricacies of DDoS attacks, deciphering their structure, motivations, and imperative fortification strategies for our digital strongholds.
What is a DDoS attack?
A distributed denial-of-service (DDoS) attack constitutes a deliberate and malicious effort to impede the regular flow of traffic to a designated server, service, or network by inundating the target or its adjacent infrastructure with an overwhelming volume of internet data.
The potency of DDoS attacks lies in their utilization of numerous compromised computer systems as sources of attack traffic. Machines vulnerable to exploitation encompass not only computers but also other interconnected resources like IoT devices.
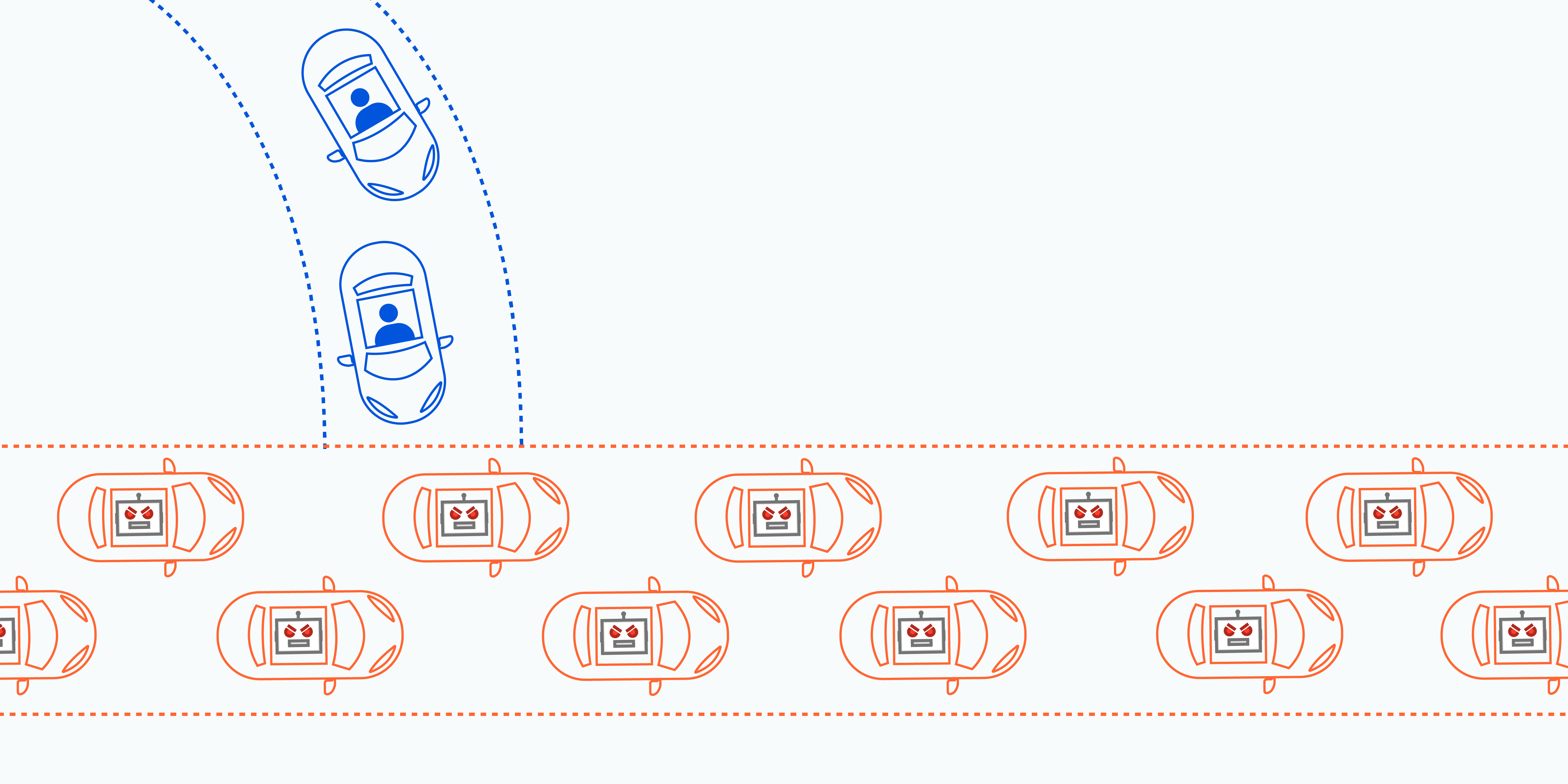
In broad terms, envision a DDoS attack as an unforeseen traffic bottleneck obstructing the highway, hindering the normal progression of traffic to its intended destination, ie the main objective of a DDoS attack is to shut down your application's ability to function by overwhelming the system to the point it can no longer operate.
How does a DDoS attack work?
DDoS attacks are orchestrated through interconnected networks of Internet-enabled machines. These networks comprise computers and various devices, including IoT devices, that have fallen victim to malware, enabling remote control by an attacker. These individual devices are commonly referred to as bots (or zombies), and the collective assembly of bots forms a botnet.
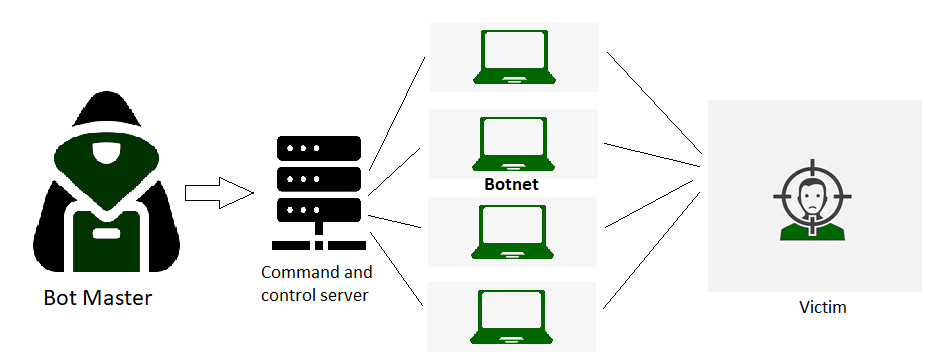
Once a botnet is established, the attacker gains the capability to orchestrate an attack by remotely issuing instructions to each bot. When targeting a victim's server or network, each bot within the botnet sends requests to the target's IP address. This influx of requests has the potential to overwhelm the server or network, leading to a denial-of-service situation for regular traffic.
The challenge arises in distinguishing the attack traffic from legitimate traffic since each bot operates as a genuine Internet device.
Example: In the year 2000, Michael Calce, a 15-year-old individual operating under the alias "Mafiaboy," orchestrated one of the initial instances of a distributed denial-of-service (DDoS) attack. Calce infiltrated the computer networks of multiple universities, leveraging their servers to execute a DDoS assault that resulted in the disruption of prominent websites, including eBay and Yahoo.
Fast forward to 2016, Dyn, a notable internet infrastructure provider, fell victim to an extensive DDoS attack. This assault had widespread consequences, causing the temporary unavailability of major online platforms and services such as Netflix, PayPal, Amazon, and GitHub.
DoS
DoS stands for Denial of Service. It is a type of attack on a service that disrupts its normal function and prevents other users from accessing it. The most common target for a DoS attack is an online service such as a website, though attacks can also be launched against networks, machines, or even a single program.

Difference between DoS and DDoS
Some of the common differences between DoS and DDoS are mentioned below.
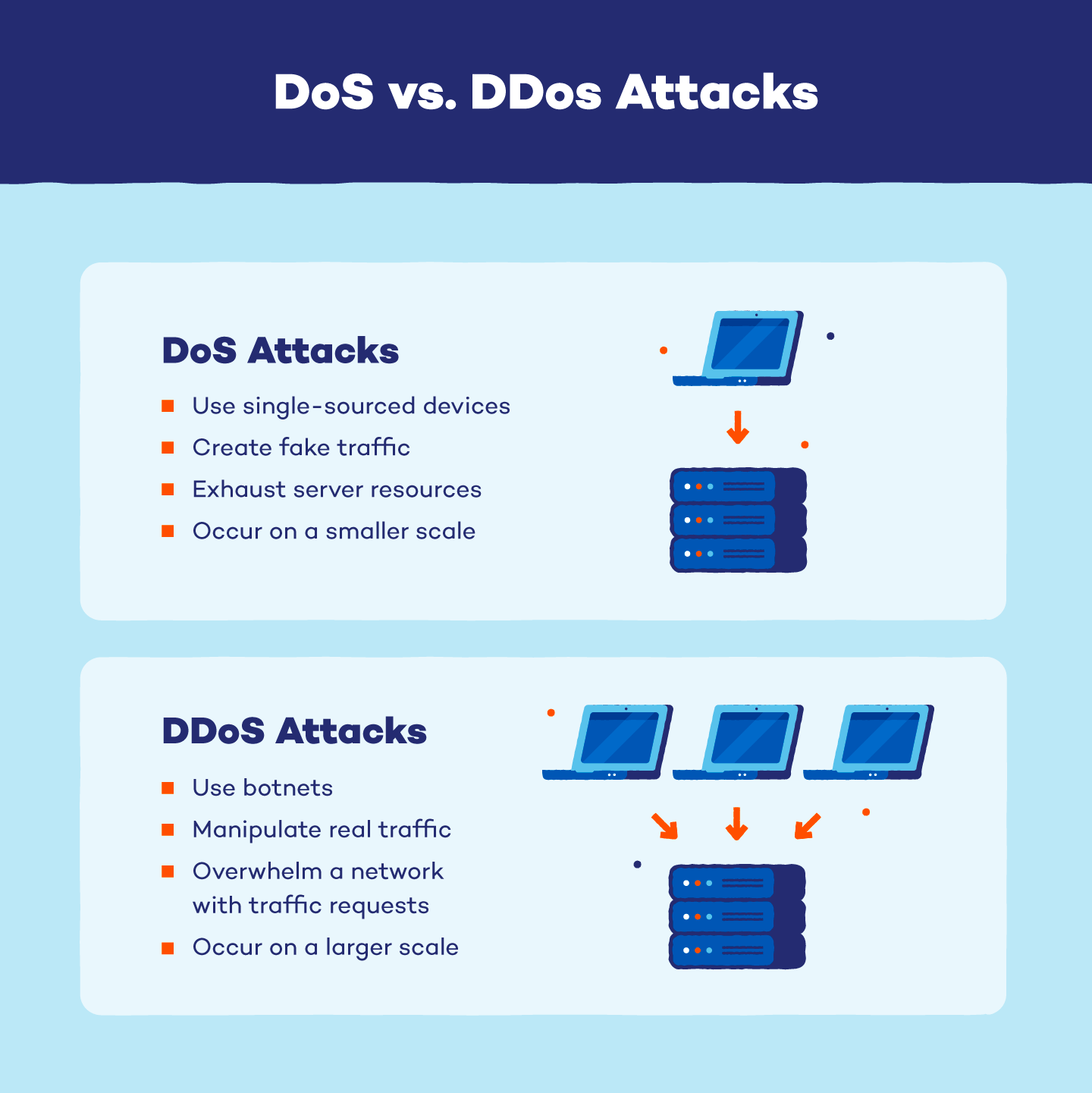
| DoS | DDoS |
| DoS Stands for Denial of service attack. | DDoS Stands for Distributed Denial of service attack. |
| In Dos attack single system targets the victim system. | In DDoS, multiple systems attack the victim’s system. |
| Victim’s PC is loaded from the packet of data sent from a single location. | Victim PC is loaded from the packet of data sent from Multiple locations. |
| Dos attack is slower as compared to DDoS. | A DDoS attack is faster than DoS attack. |
| Can be blocked easily as only one system is used. | It is difficult to block this attack as multiple devices are sending packets and attacking from multiple locations. |
| In DOS Attack only a single device is used with DOS Attack tools. | In a DDoS attack, The volumeBots are used to attack at the same time. |
| DOS Attacks are Easy to trace. | DDOS Attacks are Difficult to trace. |
| Types of DOS Attacks are: | Types of DDOS Attacks are: |
Detecting a DDoS Attack
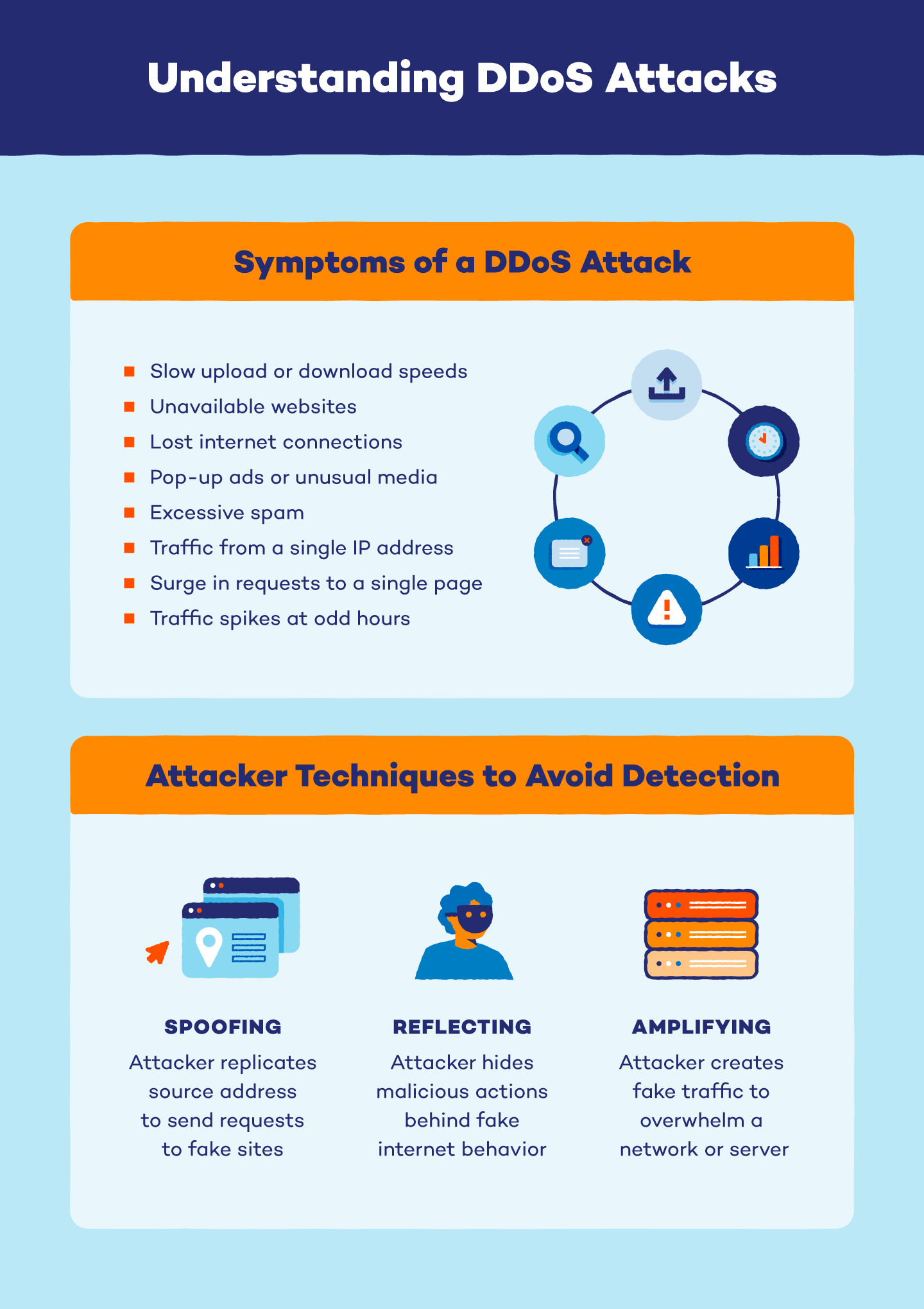
The primary indicator of a distributed denial-of-service (DDoS) attack is a sudden slowdown or unavailability of a website or service. However, several factors, including a legitimate increase in traffic, can result in similar performance issues. Employing traffic analytics tools can help in identifying key indicators of a DDoS attack:
Unusual Traffic Volume: Detection of suspiciously high levels of traffic originating from a single IP address or a specific IP range.
Behavioral Anomalies: Recognition of a flood of traffic from users exhibiting a singular behavioral profile, such as shared device types, geolocations, or web browser versions.
Surge in Requests: Observation of an unexplained increase in requests directed towards a particular page or endpoint.
Abnormal Traffic Patterns: Identification of peculiar traffic patterns, such as spikes occurring at odd hours of the day or patterns that appear unnatural (e.g., consistent spikes every 10 minutes).
There are other, more specific signs of DDoS attacks that can vary depending on the type of attack.
Common types of DDoS attacks
Various forms of DDoS attacks focus on different elements within a network connection. To comprehend the workings of diverse DDoS attacks, it is imperative to grasp the structure of a network connection.
The architecture of a network connection on the Internet comprises multiple components, often referred to as "layers." The OSI model, illustrated below, serves as a conceptual framework for delineating network connectivity across seven discrete layers.
To know about the OSI Models in detail please read my blog here.
Although the common denominator in almost all DDoS attacks is the inundation of a target device or network with traffic, these attacks can be categorized into three distinct types. An assailant may employ one or multiple attack vectors, adjusting or cycling through these vectors in response to countermeasures implemented by the targeted entity.
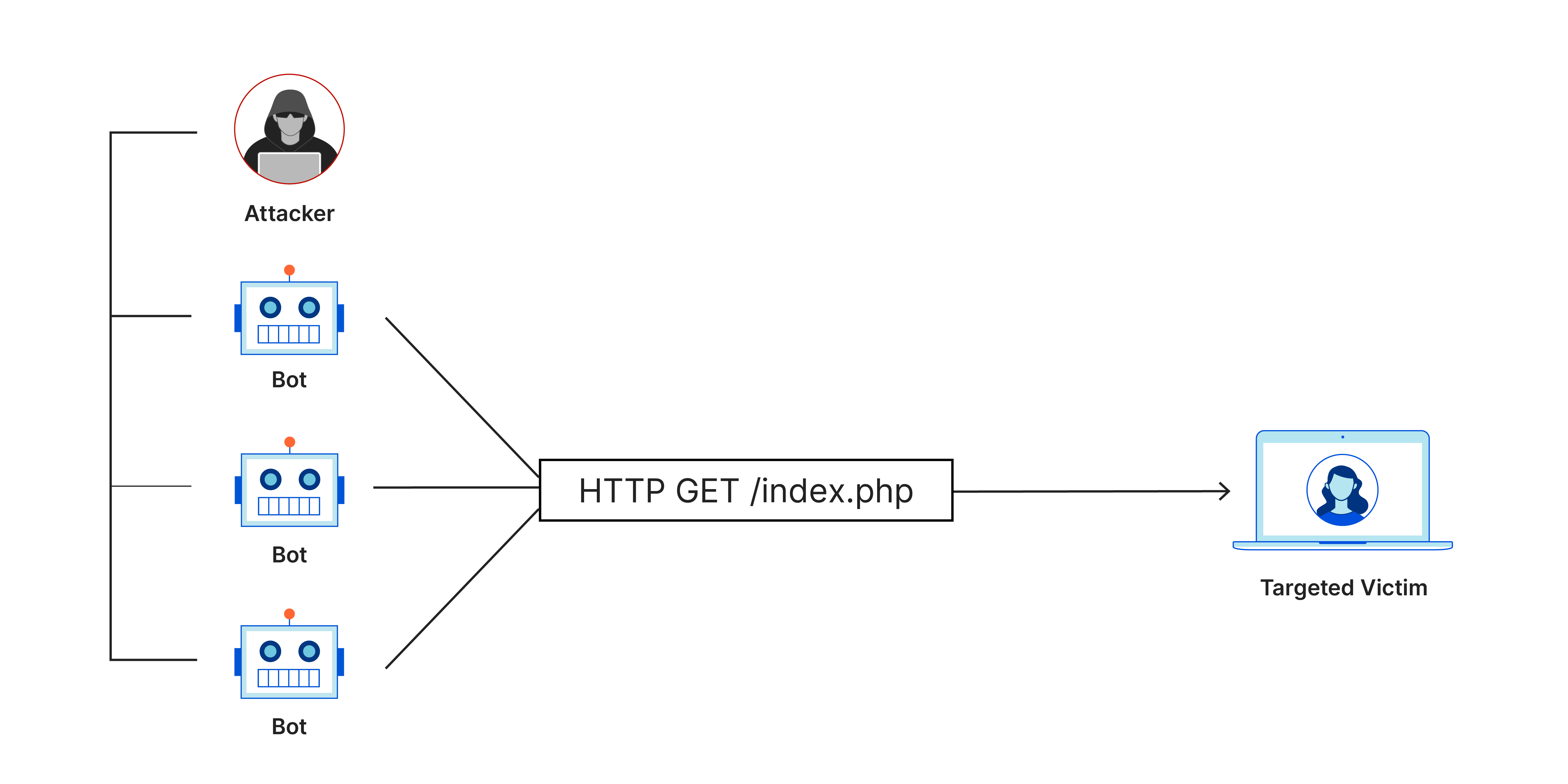
Application layer attacks
Termed as a layer 7 DDoS attack, denoting its association with the 7th layer of the OSI model, these attacks aim to deplete the resources of the target, inducing a denial-of-service condition.
These assaults specifically focus on the layer responsible for generating web pages on the server and providing them in response to HTTP requests. While a single HTTP request is relatively inexpensive to execute on the client side, it can incur substantial costs for the target server to respond to. This is because the server often loads multiple files and executes database queries to construct a web page.
Defending against layer 7 attacks poses challenges due to the complexity of distinguishing malicious traffic from legitimate traffic, making it a formidable task to mitigate and counteract such assaults.
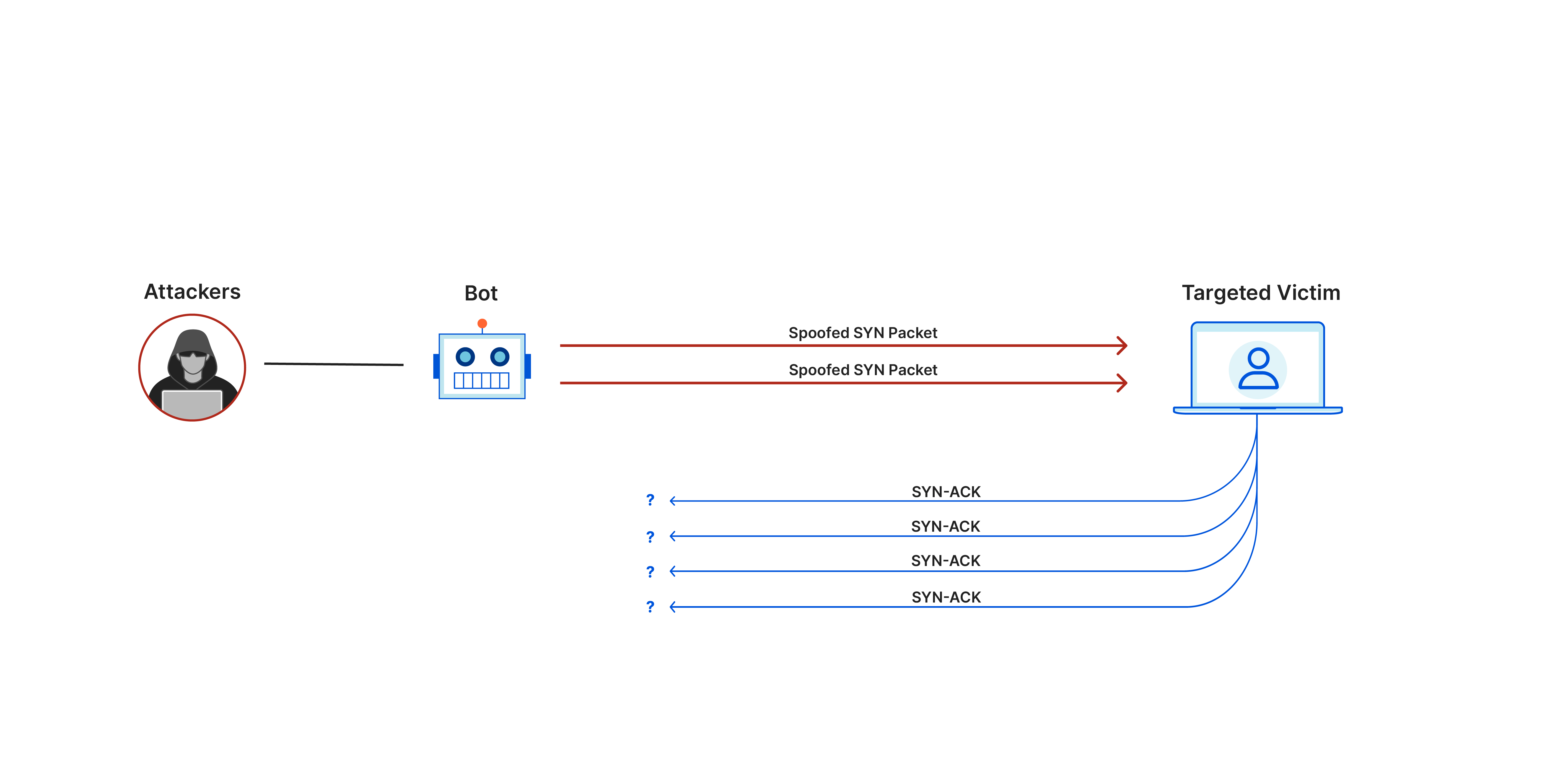
Protocol attacks
Protocol Attacks, alternatively recognized as state-exhaustion attacks, induce service disruptions by depleting server resources and/or the resources of network equipment such as firewalls and load balancers.
These attacks strategically exploit vulnerabilities in layers 3 and 4 of the protocol stack, effectively rendering the target inaccessible.
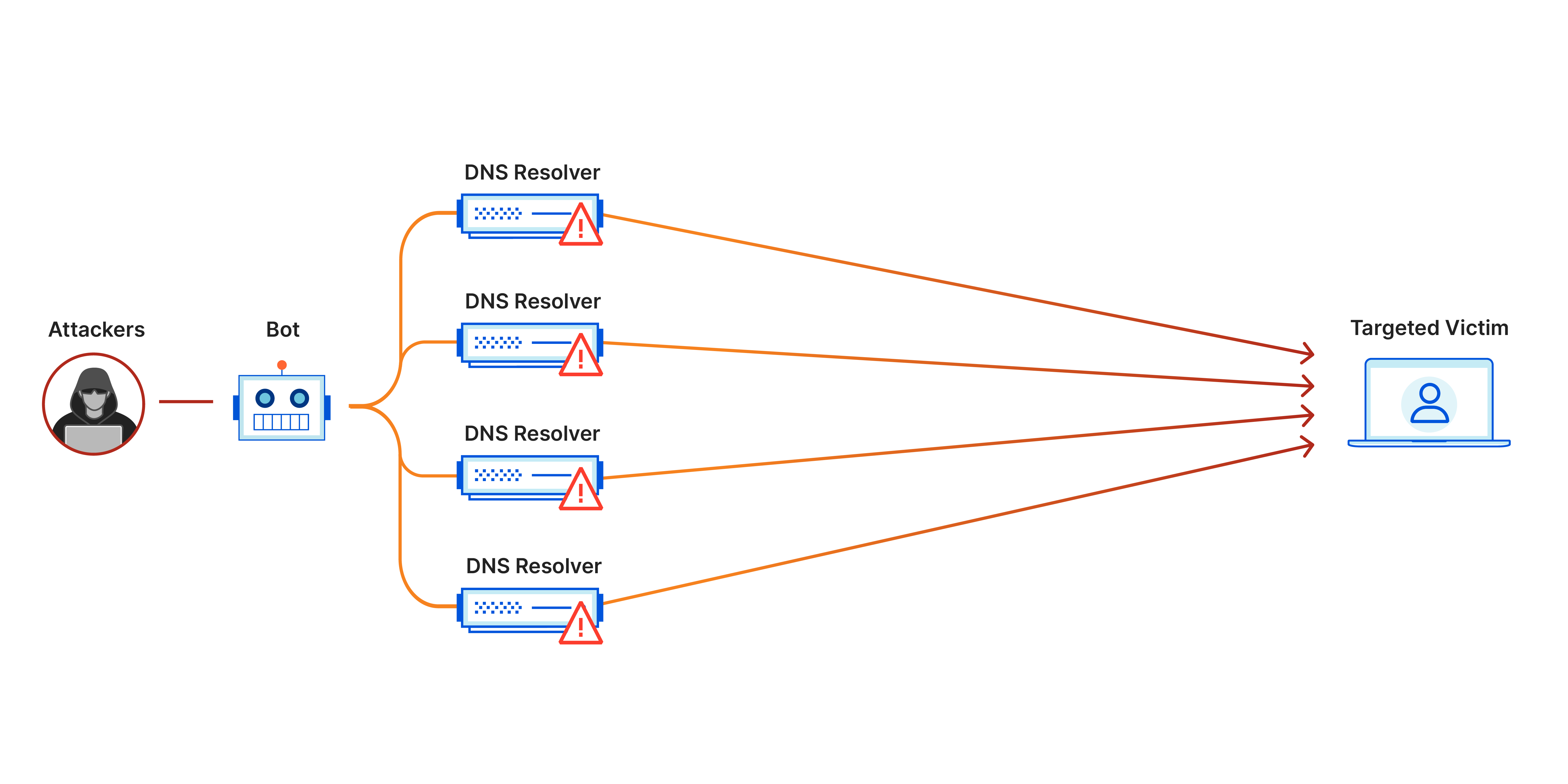
Volumetric or Amplification attacks
An Amplification Attack is a type of DDoS attack that uses various internet protocols to multiply the size of each request sent to overwhelm a network’s bandwidth. It involves the transmission of substantial data volumes to a target, employing methods like amplification or other mechanisms capable of generating extensive traffic, such as orchestrated requests from a botnet.
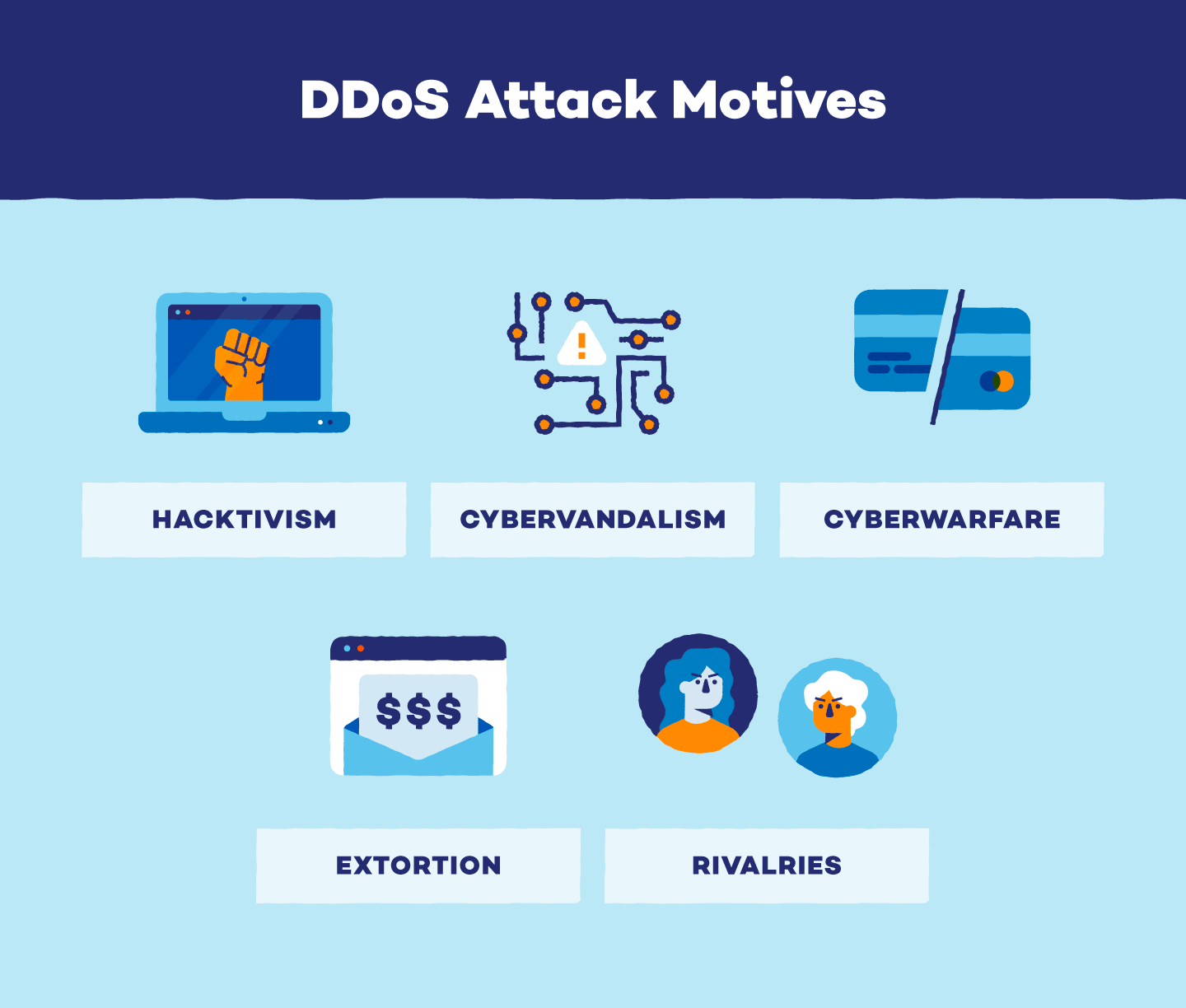
Motives for DDoSing
DDoSing — the term used when someone executes a DDoS attack — can result from a variety of motives. While these motives are different for every hacker, they can range anywhere from political gain to social justice.
Hacktivism: Hacktivists pursue social, political, or religious justice through digital activism, employing DDoS attacks as a means to further their causes.
Hacktivism: Hacktivists pursue social, political, or religious justice through digital activism, employing DDoS attacks as a means to further their causes.
Cybervandalism: Acts of cybervandalism, often lacking specific social, political, or religious motives, showcase hackers' expertise. DDoS-for-hire services may be employed to execute DDoS booters and IP stressors for online vandalism.
Cyberwarfare: In contrast to cybervandalism, cyberwarfare is characterized by political or military intent, aiming to subvert or dismantle organizational infrastructures. State-sanctioned DDoS attacks in cyberwarfare can disrupt critical sectors like finance, healthcare, and government security.
Extortion: Cybercriminals may demand resources or money under the threat of a DDoS attack. Compliance may prevent the attack, while non-compliance can lead to temporary organizational shutdowns until the threat is resolved.
Rivalries: DDoS attacks are employed as competitive tools in personal and professional rivalries, causing disruptions such as dissuading event attendance, shutting down online storefronts, and inflicting reputational damage
Mitigating a DDoS attack
Designate a DDoS Response Leader: Assign a cybersecurity lead to respond quickly to potential DDoS attacks. While prevention isn't foolproof, a rapid response is key to minimizing impact.
Use a Web Application Firewall (WAF): Deploy a WAF to combat layer 5 DDoS attacks. Acting as a reverse proxy, it shields servers from malicious traffic and can implement custom rules swiftly in response to an attack.
Detect Attacks Early: Know your typical traffic patterns to quickly identify deviations indicative of a DDoS attack. Early recognition is crucial for swift intervention.
Ensure Adequate Bandwidth: Maintain website bandwidth at 100-500% more than normal to accommodate unexpected traffic surges. While not a DDoS prevention method, it provides extra time to react before resources are overwhelmed.
Defend at the Network Perimeter: Mitigate the impact of an attack by implementing measures such as rate-limiting, adding filters, timing out connections, and dropping malicious packets. While these steps may not fully halt large DDoS attacks, they buy valuable time.
Contact Your Internet or Hosting Provider: In case of an attack, promptly inform your ISP or hosting provider for assistance. A data center managed by your provider can offer better resilience, protecting your corporate network from DDoS impact.
Engage a DDoS Mitigation Service: For large attacks, rely on a DDoS mitigation service. These services divert traffic, clean it, and forward it to your web applications, ensuring minimal downtime. Subscribing to such a service is a crucial element of DDoS attack prevention.
Develop a DDoS Playbook: Prepare for DDoS attacks by creating a comprehensive playbook. Include steps for response, contact details, DDoS mitigation services, and communication plans with customers. Running simulated attacks helps refine your response procedures, ensuring a swift and effective reaction during a real attack.
Conclusion
In the ever-changing online threats, it's important to understand how DDoS attacks work to protect our digital space. Think of it like preventing a traffic jam on the internet. By recognizing how multiple compromised systems team up to disrupt normal online traffic, we can better secure our digital roads. Using smart defense strategies and following cybersecurity rules helps us handle these online storms, keeping our digital world safe and sound.
Endcard
Thank you for joining me on this insightful blog on the DDoS Attacks
If you found this blog helpful and informative, don't forget to give it a like!
Stay updated with my latest posts and never miss out on exciting content! Click that Follow button to join and stay in the loop!
Follow me on Linkedin --> rupak1chakraborty
Stay tuned for more such content...👋🔍🌈